Body Scanner Supplier
A full-body scanner is an advanced security screening device designed to create detailed images of a person's entire body to detect concealed items such as weapons, explosives, or other contraband. This scanner is used in high-security environments such as airports, government buildings, correctional facilities, and other sensitive locations.
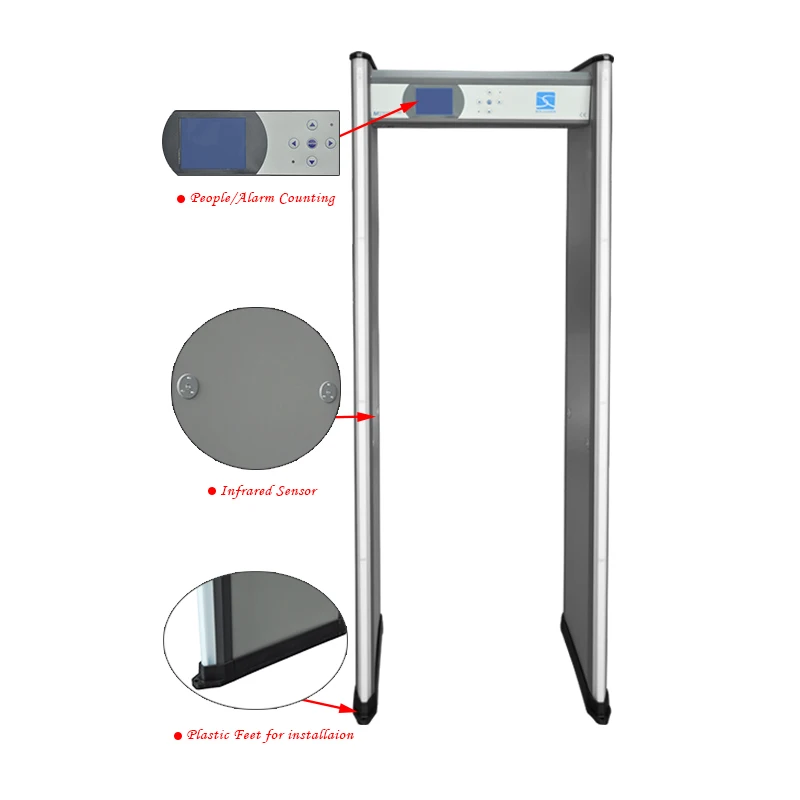
Purpose
Full-body scanners are employed for security screening to enhance the detection of concealed items that may pose a threat to public safety or security. They provide a non-intrusive means of inspecting individuals for hidden objects without the need for physical pat-downs.
Privacy Considerations
Privacy is a significant consideration in the deployment of our full-body scanner. To address concerns, many modern systems are designed to respect individuals' privacy. The images generated are often viewed remotely by security personnel, and specific anatomical details are not revealed.
Operation
A person being screened by a full-body scanner typically stands in a designated portal or chamber. The scanner emits the chosen form of energy (millimeter-wave or X-ray), and sensors capture the reflections or scatterings to create an image. The entire process is non-intrusive and takes only a few seconds.
Alarm and Alert System
Full-body scanners are equipped with an alarm or alert system that signals the presence of anomalies or objects that may require further investigation. If the scanner detects something unusual on the individual, an alarm is triggered, prompting security personnel to conduct a more thorough examination.
Integration with Access Control Systems
In high-security environments, full-body scanners are often integrated with access control systems. This integration ensures that individuals who have undergone the necessary security screening are granted access to specific areas within a facility.
Full-body scanners contribute to enhancing security measures by providing a more comprehensive and efficient means of screening individuals for concealed items. The technology has evolved to address privacy concerns and comply with regulatory standards while maintaining a high level of accuracy in threat detection.
